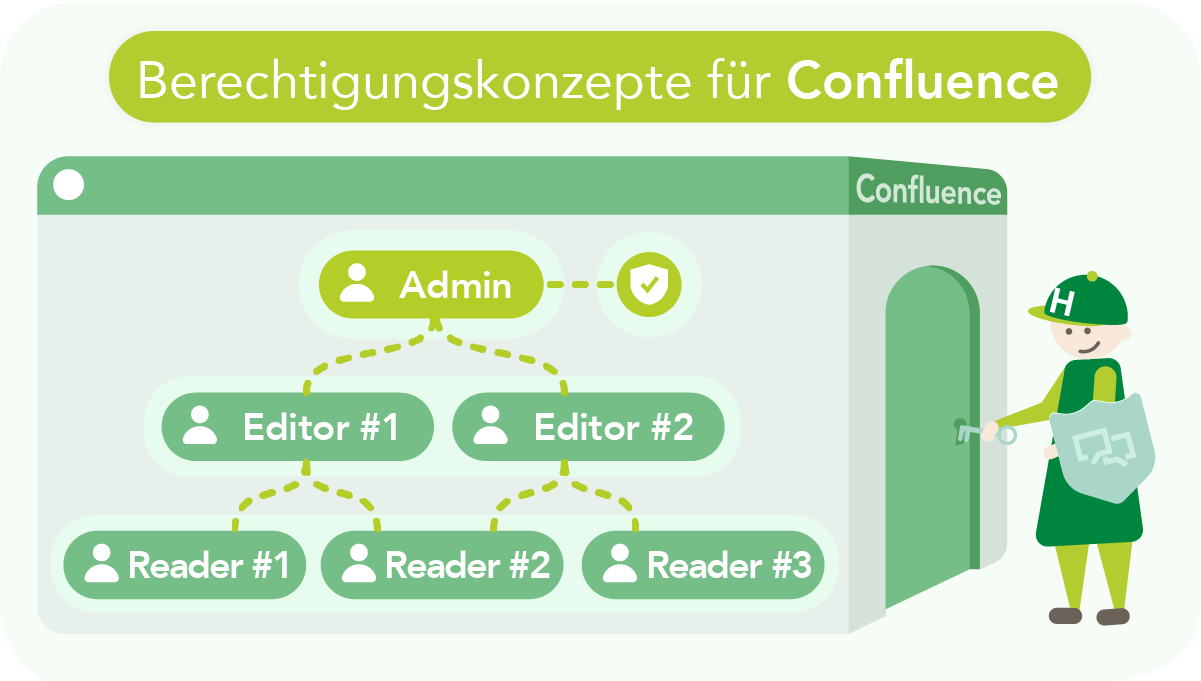
Permission chaos in Confluence
When multiple teams and departments in a company access Confluence at the same time, things can quickly descend into a confusing tangle of permissions: too many administrators, unclear responsibilities, and pages that are no longer findable or are accidentally visible to unauthorized people. This can lead to serious problems: suddenly, confidential information is exposed to everyone, onboarding new employees takes unnecessarily long, and internal processes stall because no one is quite sure who actually has access to what—or is allowed to. Not infrequently, such situations end with security risks, compliance violations, and a growing mountain of administrative overhead.
A well-thought-out permissions structure in Confluence is easy to implement – provided you take a structured approach and plan for the future.
Why a rigorous permission model
is so crucial
A well-designed permission model first and foremost creates order and transparency. Everyone knows which information they can access and why, and who is allowed to create a new space or page. This reduces the risk of accidental data leaks, and everyone involved can collaborate more efficiently. In addition, compliance requirements are easier to meet because confidential content is made accessible only to specific groups of people.
In addition, a sustainable model provides room for growth and change. Whether new employees join, departments are restructured, or an integration with Jira is planned: if roles and groups are clearly defined, you can respond flexibly and maintain oversight of projects and Confluence spaces.

The key steps to set it up
- Clarify goals and requirements: Consider which content is particularly sensitive and how you want to protect it. Are there legal requirements or internal compliance rules? Who are the stakeholders that need access to specific spaces?
- Define roles and groups: Establish clear responsibilities by defining roles such as “Confluence Administrator”, “Space Administrator” and “Editor”. Also consider which groups in Confluence (and possibly in Jira) can be used to manage permissions effectively.
- Set global and space permissions: Define who has global access to Confluence and who may create spaces. At the space level, assign read, edit, and admin rights to the previously defined groups and roles.
- Use page restrictions judiciously: Too many individual page permissions can quickly lead to chaos. Instead, create dedicated, clearly defined spaces for sensitive content and avoid creating too many exceptions.
- Documentation and training: Document your permission model in a central place and ensure that everyone who works with permissions in Confluence is adequately trained. Only then will structures remain clear and secure in the long term.
- Regular review and maintenance: A permission model is never finished. Employees leave the company, projects are archived, or new departments are created – all of that must be reflected in the permissions so that nothing gets out of hand.
A simple example
A sustainable permission model in Confluence often starts with general groups such as “Admins”, “Editors” and “Readers”. This foundation is suitable for smaller organizations with clear hierarchies. As the company becomes more structured, groups should be named more specifically – for example, “Editor-Marketing” or “Reader-IT” – and assigned to the respective spaces accordingly. This way, employees receive edit rights in their own spaces and read-only rights in others. As the organization grows, complexity increases, for instance when departments like IT are further subdivided. Thanks to descriptive group names such as “Editor-IT-Infra”, the model remains understandable and maintainable even as changes occur.
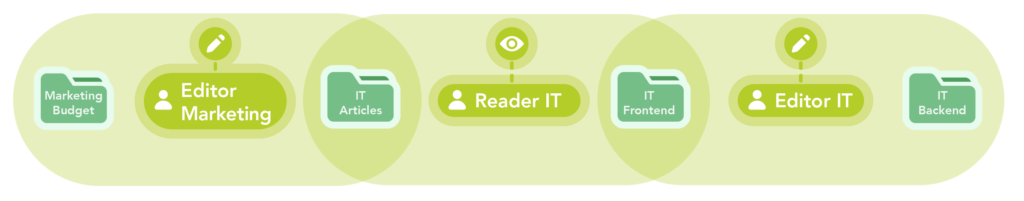
In reality, it can often make sense not to tie groups and spaces to departments. Our experience has shown that different companies take different approaches to this topic. Our goal is achieved when we have implemented a permission model that meets our customers’ requirements and is also transparent, sustainable, and maintainable.
Professional support with a focus on sustainability
Planning or realigning a permission model can seem complicated at first glance. Especially with a view to sustainable use, it is worth establishing a well-thought-out structure early on. Neutral consulting provides orientation and ensures that security, compliance and efficient collaboration go hand in hand over the long term.
Here’s how we proceed:
- Assessment: Together, we review your current permission assignments and examine how they can be embedded into a new, future-proof model.
- Design: Taking your requirements into account, we create a clear role model, complemented by meaningful groups – ideally designed so that it can also be extended to other tools like Jira.
- Implementation: We support the technical rollout step by step and ensure that all users receive exactly the access rights they need for their work.
- Training and documentation: A concept is only as good as the people who work with it. That’s why training and clear instructions for everyone involved are part of successfully implementing a permission system – so that permission management remains understandable and secure in the long term.
A well-thought-out permission model for Confluence not only increases security and clarity, but also saves time in the long run and avoids unnecessary risks. If the first signs of ambiguities in permission assignment are already visible in your company, or you want to make the system future-proof from the start, it’s worth taking a focused look at growth and further development. Striking a balanced compromise between user-friendliness and security is crucial. If you need support, you can rely on our professional consulting to jointly develop a sustainable structure and thus benefit in the long term from reliable permission management.