- BSI Baseline Protection provides the framework for legally compliant information security in authorities – from federal agencies to municipal administrations.
- The IT Baseline Protection Compendium with 111 modules structures management tasks, organizational rules, and technical safeguards across ten layers.
- Honicon’s 4-step method connects BSI Baseline Protection with Atlassian tools: Analysis → Concept → Integration → Operations for sustainable ISMS operation.
- Jira, Confluence & Assets map workflows, documentation, and target objects – without feeling like a foreign body in everyday administrative work.
From compliance requirements to lived IT security
Federal authorities, state authorities, and municipal administrations are under increasing pressure. NIS 2, the BSI Act, sector-specific security standards, and internal audit requirements are bringing IT Baseline Protection to the forefront. For many organizations in the public sector, this initially sounds like yet another documentation obligation. At the same time, awareness is growing: without a resilient level of information security, government action falters and digital administrative modernization remains a patchwork rather than a success story.
BSI Baseline Protection provides the framework for an ISMS in the public sector. Standards 200-1, 200-2, and 200-3 define the management system, methodology, and risk analysis; the IT Baseline Protection Compendium structures modules for processes, systems, and infrastructure. Together, this combination creates a toolbox for legally compliant information security in authorities—provided that structures, roles, and tools interlock cleanly.
Common challenges in everyday administrative work
Many organizations face staff shortages, particularly in information security. Data protection, IT operations, e-government, line-of-business applications, identity management—specialists juggle topics that would each justify a full-time mandate. Additional requirements from IT Baseline Protection and NIS 2 are added on top.
Complexity shapes daily operations: historically grown data centers, hybrid structures combining on-premises and cloud, long-running line-of-business applications, parallel worlds of legacy systems and new platforms. Every module in the IT Baseline Protection Compendium meets a unique landscape; no template fits without adaptation.
Budget constraints exacerbate the situation. Investment funds flow into line-of-business applications and citizen portals; information security competes with visible projects. Nevertheless, oversight bodies expect an ISMS based on a recognized methodology, often with a concrete goal such as “IT Baseline Protection for authorities” or “ISMS for the public sector.”
Module structure as an organizing framework
The BSI IT Baseline Protection Compendium is at the heart of every certification according to BSI Baseline Protection. The current edition comprises 111 modules across ten layers. The layers range from security management (ISMS), organization and personnel (ORP), concepts and methodologies (CON), through operations (OPS) and detection/response (DER), to infrastructure (INF), networks (NET), IT systems (SYS), applications (APP), and industrial IT (IND). This provides a framework that describes management tasks, organizational rules, and technical safeguards within a unified system.
The modules are divided into process-oriented and system-oriented elements. Process-oriented modules address the entire information domain or large parts of it, such as security management, personnel organization, or operations. System-oriented modules target specific assets such as servers, networks, line-of-business applications, buildings, or control centers. Each module describes typical threats, formulates requirements, and adds examples of suitable measures. In this way, a consistent set of rules is created for each layer that translates directly into everyday administrative practice.
Over the course of a project, the focus is not on freely selecting individual modules at will. What matters is modeling the information domain in accordance with BSI Standard 200-2. Business processes, applications, IT systems, rooms, and communication links form the starting point. For each of these assets, the project team assigns the modules that fit thematically. Step by step, a complete model of the scope emerges. The number of relevant modules therefore results from the structure and size of the authority, not from a rigid specification.
The layers of the compendium also suggest a sequence. First, the organization comes into focus: security strategy, roles, responsibilities, training. This is followed by operations, detection, and response. Only then do the technical layers— infrastructure, networks, systems, and applications—build on top. An information domain with modules consistently implemented across all affected layers does not show isolated solutions, but a coherent picture of information security. For certification based on IT Baseline Protection, this interplay is decisive: all modules anchored in the model within the scope are implemented and supported by appropriate evidence.
From requirement to implementation: 4-step method
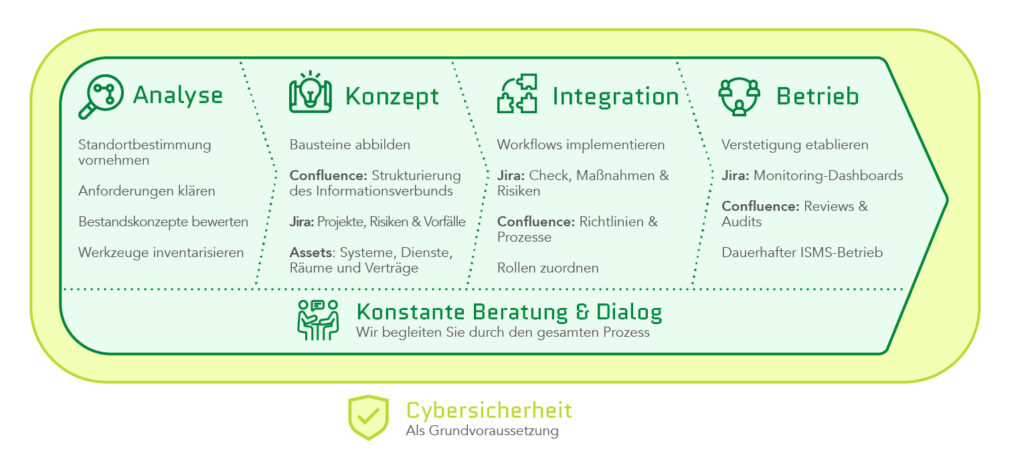
For years, Honicon has worked with Jira, Confluence, and Assets in the context of public-sector clients. From this practical experience, a 4-step method emerged that connects BSI Baseline Protection with Atlassian tools, creating a tangible ISMS for authorities.
The first step is establishing the baseline. This includes reviewing applicable legal obligations, existing policies, current security concepts, and tools already in use. For federal authorities, NIS 2 and BSI Baseline Protection take center stage; for municipal administrations, state-level requirements, municipal associations, and audit requirements are added.
The second step focuses on modeling according to the module structure. The information domain, structural analysis, and protection needs assessment are placed in Confluence. Modules from the IT Baseline Protection Compendium are assigned to assets: line-of-business applications, server landscapes, networks, properties. Jira supports projects for measures, risks, and incidents. Assets maps systems, services, rooms, and contracts.
The third step is integration into everyday administrative work. Workflows in Jira reflect IT Baseline Protection processes: from handling deviations in the IT Baseline Protection check, through managing measures, to risk analyses in accordance with BSI Standard 200-3. Confluence documents policies, process descriptions, and committee minutes. Organizational roles—information security officers, data protection, IT operations, business owners—receive assigned tasks within these workflows.
The fourth step focuses on sustainability. Dashboards in Jira show open measures, overdue reviews, and risks with high net risk. Confluence spaces for management reviews, internal audits, and training support continuous improvement. In this way, a project phase grows into sustainable ISMS operations that combine legally compliant documentation with lived processes.
Jira is well suited as a central instrument for activities related to IT Baseline Protection. Deviations from the IT Baseline Protection check, findings from internal audits, implementations from risk analyses, security incidents, emergency exercises—all of these run through structured, defined workflows. Transparent responsibilities, deadlines, and escalation paths replace scattered emails.
Confluence serves as the knowledge and documentation base. The IT security policy, guideline on BSI Baseline Protection, process descriptions, emergency manual, minutes from information security committees, evidence of training and awareness—all of this is housed in structured spaces with clear permissions. Templates ensure consistent structure; labels enable quick retrieval.
Assets maps technical and organizational assets. Line-of-business applications, servers, networks, properties, service providers, contracts, responsible parties—everything appears as objects with attributes and relationships. Risks, measures, and incidents are linked to these objects. This creates a picture that shows not only IT, but the entire information domain.
Honicon is familiar with both Confluence Cloud and Confluence Data Center. The same applies to Jira and Assets. Interfaces can be designed to be more technical or more user-friendly as needed, for example through apps like Aura or Mantra. Departments receive landing pages, tiles, and guided navigation paths, while experts use detailed views and technical representations.
Honicon: Thinking Forward for public administration
Honicon sees itself as a partner for IT Baseline Protection in public administration. The process consulting team brings together experience with Atlassian tools, information security, and administrative structures. A BSI Baseline Protection–certified staff member supports clients as an external information security officer, moderates risk analyses, accompanies IT Baseline Protection checks, and ensures documentation that integrates seamlessly.
The core message is: legally compliant implementation of BSI Baseline Protection with proven Atlassian tools – Thinking Forward for public administration.
Honicon offers a free initial consultation and a compact BSI readiness assessment for the public sector. This gives every organization a clear view of its current status, gaps in IT Baseline Protection, and concrete next steps toward a resilient ISMS in line with BSI Baseline Protection, NIS 2, and modern information security in administration.