- BSI-Standard 200-1 prioritizes systematic management over individual measures and anchors information security as a leadership responsibility.
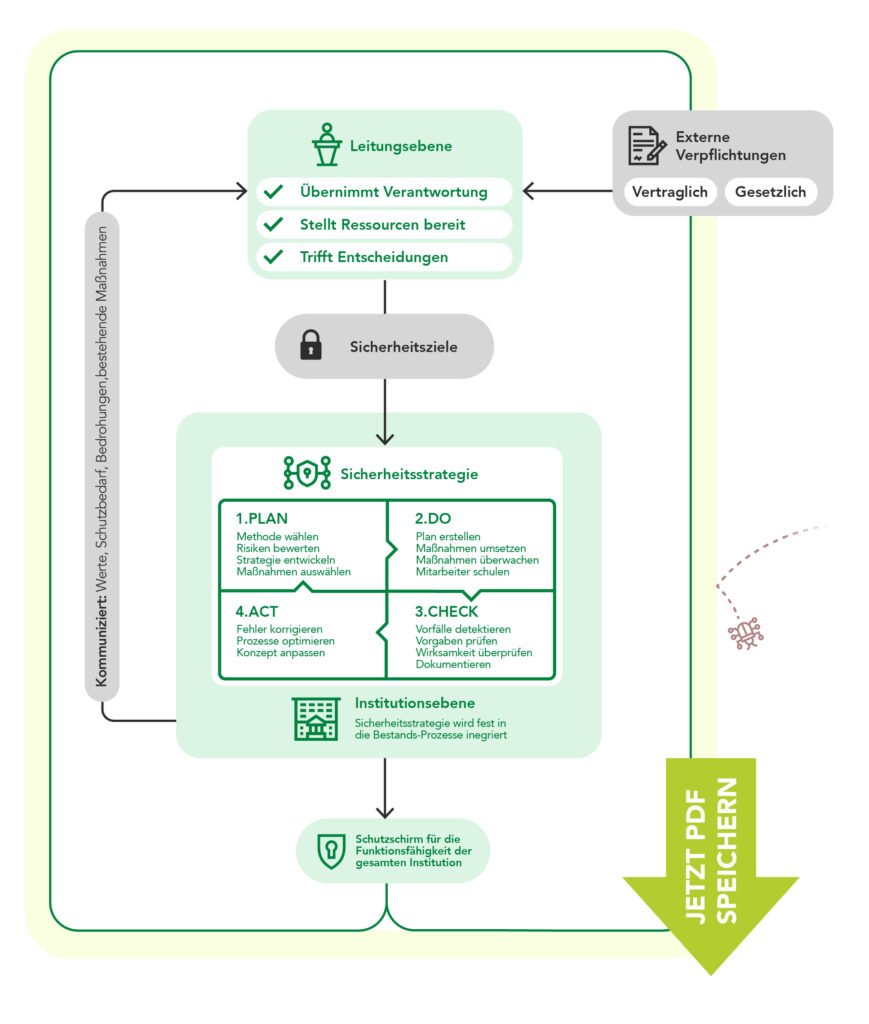
- The executive level decides on risks, resources, and information security objectives and ensures integration into existing structures.
- Honicon designs processes so that the requirements of BSI Standard 200-1, ISO standards, and legal obligations are met, and an ISMS emerges without feeling like a bolt-on.
- Jira, Confluence & Assets support traceability, governance, and evidence, especially in authorities and public-sector organizations.
BSI Standard 200-1 describes the basic framework for an information security management system. At its core is a systematic approach: An appropriate level of security arises primarily through clear responsibilities, traceable processes, and recurring management cycles, and only then through individual technical measures. The standard aligns with ISO/IEC 27001, uses terminology from ISO/IEC 27000, and follows the recommendations of ISO/IEC 27002. For authorities and public-sector organizations, this creates a framework that links international standards with German administrative practice.
What the BSI Standard 200-1 requires
The standard focuses on what constitutes effective information security management. Decisive factors are leadership responsibility, clear objectives, structured planning, and a regulated improvement process. Information security is not isolated but accompanies the key business processes and tasks of an institution.
Core points of the standard:
The executive level is responsible for compliance with legal requirements and contractual obligations. Disruptions in critical business processes affect not only individual IT components, but the ability to deliver to citizens and partners. In this context, information security serves as a protective umbrella for the institution’s overall ability to function.
The executive level makes decisions on how to deal with risks. The basis is a structured overview of assets, protection needs, threats, and existing measures. On this basis, security objectives and a security strategy are developed. The standard requires a traceable derivation: The reasons for risk treatment, risk acceptance, or prioritization must be clearly on the table.
Security objectives are not abstract; they lead to concrete packages of measures. The standard asks how the selection of measures and security concepts come about. Organizational rules, training, technical safeguards, and monitoring functions interlock. Documentation at an appropriate level of detail forms the basis for evidence to supervisory bodies, internal audit, and external auditors.
Another key element concerns maintaining and further developing the achieved level of security. BSI Standard 200-1 takes a cyclical view of information security. Plan, Do, Check, Act — this sequence shapes all levels of the ISMS. Management reviews, internal audits, and a structured handling of nonconformities ensure continual improvement.
The role of the executive level
The standard emphasizes the special role of the executive level. This is where responsibility for legal compliance, fulfillment of contracts, the functionality of business processes, and economical use of resources comes together. Information security interfaces with HR, organization, IT, procurement, facility management, and communications. Only leadership can provide coherence across them.
Integrating the ISMS into existing structures is a guiding principle. Information security does not stand alongside the organization; it runs through it. The standard calls for embedding into existing decision paths, committees, planning routines, and reporting lines. Information Security Officers, data protection, specialist departments, IT, and internal audit need aligned roles, not parallel silo structures.
The standard also addresses resource matters. Information security costs time, staff, and budget. The executive level sets priorities and is accountable for the economical use of these resources. Decisions on investments, additional staff, or project priorities are not made on gut feeling, but in the light of protection needs, risks, and strategic direction.
Honicon’s approach: processes at the center
Honicon works as a small IT consulting firm with roots in process consulting. Experience lies in designing and documenting processes and in using Jira, Confluence, Assets, and other components from the Atlassian ecosystem. The team includes trained staff certified as external Information Security Officers. Projects with counties, public-law special-purpose associations, municipal enterprises, and other organizations under public ownership shape this profile.
Against this background, a clear approach to implementing BSI Standard 200-1 emerges. The starting point is always the existing organization. Processes take a form that meets the standard’s requirements while keeping efficiency in view. The goal: an ISMS fits into existing structures and does not feel like a foreign body.
Jira is suitable as a platform for governance and traceability. Measures, risks, exceptions, approvals, and orders run there in defined workflows. Responsible parties are transparent, deadlines are visible, and status reports are created without additional writing effort. Confluence serves as the knowledge and policy repository. The security policy, guidelines, procedures, minutes from meetings, and collections of outcomes have a clear home; versioning and permissions remain traceable. Assets complements this setup with structured information on systems, applications, interfaces, locations, and responsible parties.
Process perspective and tool use go hand in hand. Where the standard demands a clear line between planning, implementation, control, and improvement, Honicon implements concrete workflows with Atlassian tools. For example, risk analyses, decisions on risk acceptance, follow-up tasks, and implementation evidence can be represented in a coherent issue flow. This gives the executive level insight into the security status without having to track every detail.
Practical implementation for public-sector clients
Authorities and publicly owned companies have their own framework conditions: budget law, procurement requirements, political steering, supervisory boards, and sometimes complex ownership structures. Honicon knows these specifics from projects with counties, municipal IT service providers, and enterprises in public ownership. Information security intersects there with administrative modernization, digitization mandates, NIS-2, BSIG, and KRITIS regulations.
BSI Standard 200-1 provides orientation in this environment. It answers questions about success factors for managing information security, about appropriate governance of the security process, about developing security objectives and strategy, about the selection of measures, and about safeguarding the level achieved. Honicon translates these requirements into practical processes and structures.
The executive level receives a clear basis for decision-making, Information Security Officers work with tools that support daily work, and departments see information security as part of their normal process. Step by step, an ISMS in the sense of BSI Standard 200-1 emerges: manageable, governable, and auditable — while being embedded in the reality of an authority or a public enterprise.