Many companies that previously did not consider themselves “critical” are suddenly in the spotlight of European cybersecurity regulation. IT management, executive leadership and security officers in medium-sized companies are currently asking: Are we affected by the NIS-2 Directive – and what exactly does that mean for us?
On 30. Juli 2025, the Federal Office for Information Security (BSI) published the draft bill for implementing the NIS-2 Directive. This significantly expands the previous scope. Many companies – especially from sectors such as manufacturing, mechanical engineering, IT services, logistics or healthcare – are now coming more into focus within the EU’s cybersecurity strategy. Companies that have not previously been subject to specific legal requirements in the area of IT security will in future be actively included in the protection of digital infrastructures.
In Germany, according to the Federal Ministry of the Interior, this will affect around 29.000 companies and institutions.
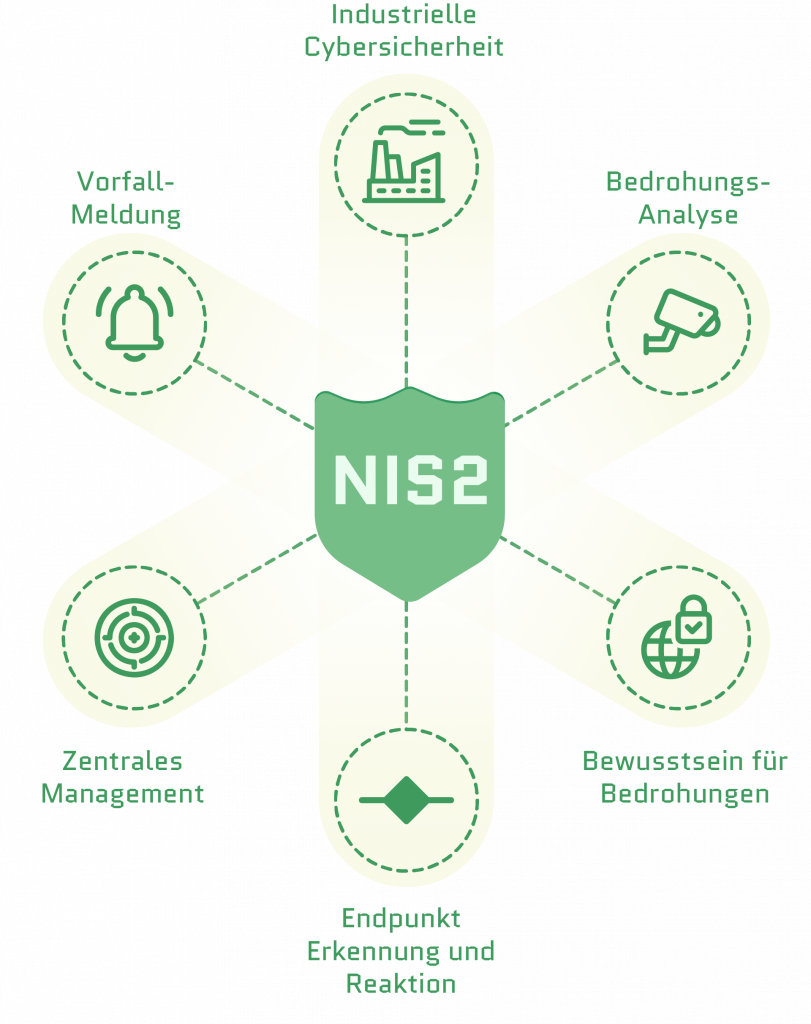
What changes with NIS-2
The draft provides that companies must meet certain minimum requirements for their cybersecurity. Here are the key points:
- Obligations for many mid-sized companies: Companies with as few as 50 employees or 10 Mio. Euro in annual revenue may be affected – depending on their sector.
- Mandatory risk management: IT security measures must be documented and reviewed regularly.
- Reporting obligations for security incidents: Events with potential risk to customers, partners or supply chains must be reported to authorities – tiered and time-bound.
- Liability of management: Managing directors will bear a much more visible responsibility.
- Tight timeline: The law is slated to be passed in 2025 and become fully effective from 2026 onward.
At first glance, that may sound like a lot of work for some businesses. But for many companies this development also offers an opportunity: They now fall within a legal framework that clarifies what “appropriate” IT security means. Instead of relying on isolated measures or intuitive assessments, companies can align their security strategy with binding standards – and thus not only meet regulatory requirements, but also strengthen the trust of customers, partners and investors.
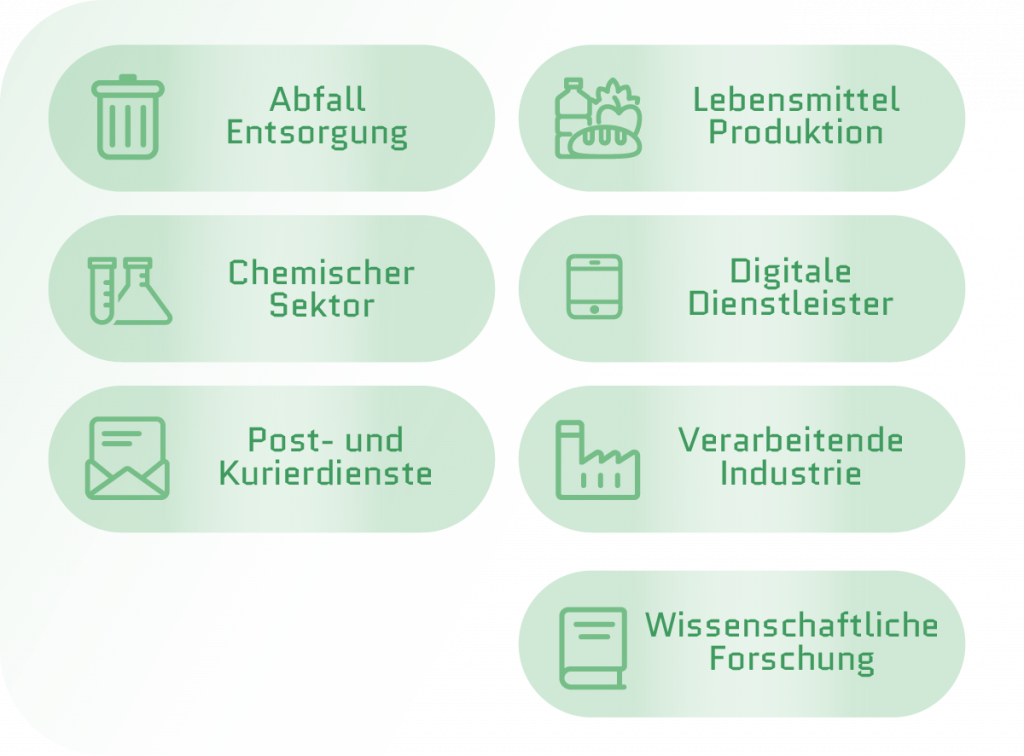
“Important entities” are required to register with the joint registration office of BSI and BBK.
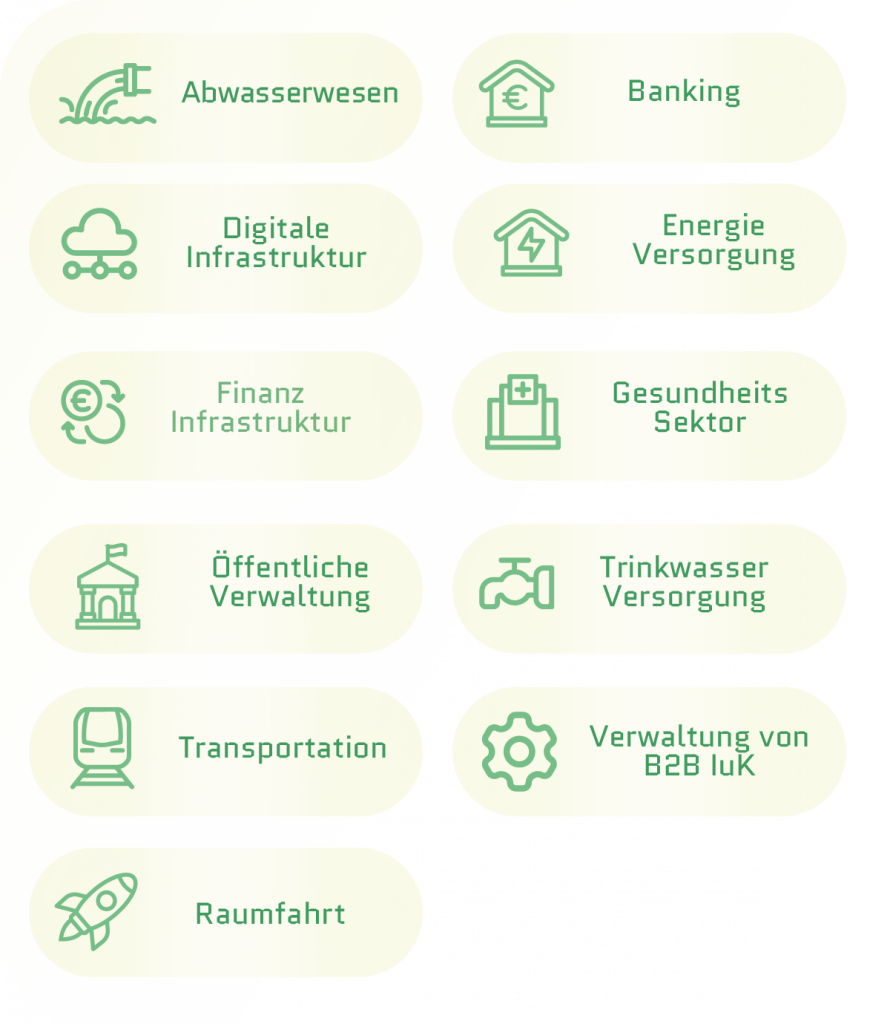
“Particularly important entities” are required to register with the joint registration office of BSI and BBK.
What this means for companies
For those who have not had to deal with the details of European IT security directives so far, complex questions now arise:
- Do we fall under the new requirements?
- Which measures do we need to implement, specifically?
- How much effort is involved – personnel, technical, legal?
- How do we protect ourselves against fines or liability risks?
The BSI provides information on most questions that can help companies. Here you can learn more. However, without experience the topic can be very complex and demanding.
But we can support you
We help companies keep an overview and implement the requirements of NIS-2 in a structured, efficient and appropriate way. Together, we can analyze whether and to what extent your company falls under the new legal framework. When we know more, we develop a strategy for realistic implementation of NIS2 for you. We prioritize measures and integrate them into existing structures. Since this is a particular focus of NIS2, we help you build a functioning reporting system with clear responsibilities and practical workflows.
It is also important to strengthen understanding within your company. Through training and courses, we enable both management and specialist departments to take action.
Whether based on ISO 27001, BSI IT-Grundschutz or sector-specific standards – we support the development of suitable processes and documentation. And we ensure that your documentation is audit-proof – for internal reviews as well as external audits.

Now is the right time to act
Medium-sized companies in particular benefit from taking action early. Those who address the requirements now can shape implementation with a sense of proportion – aligned with their own structures and resources. Instead of merely reacting to external requirements, there is the opportunity to anchor IT security strategically and remain competitive in the long term. That not only creates security, but also room to maneuver.
Implementing NIS-2 is not a short-term project, but a strategic step for many companies. Those who start planning today avoid operational rush once the law comes into force – and at the same time position themselves as a trustworthy partner in a digitally networked economy.
Honicon GmbH is at your side as an experienced, hands-on consultancy. We know the legal requirements as well as the day-to-day challenges of small and medium-sized enterprises – and we bring the two together.
If you need an informational meeting, consulting, implementation , training, or the complete package on the topic of cybersecurity, then talk to us.
Schedule a conversation –
Security that pays off
