Cleverly manage identities in the company
Companies are increasingly concerned with meeting compliance and audit requirements by simple and comprehensible means. Identity management and authorization management continue to be the focus of these efforts. It is precisely here that glaring gaps are repeatedly found in security audits or in routine checks as part of ISO27001, for example. In our consulting work, we are also repeatedly confronted with the question of whether the resources contained in Jira Service Management can be used to manage identities. In this series of articles, we would like to take a closer look at this very topic and show which tools we are already using successfully with customers and what opportunities they offer. This is part 1 of the 4-part series.
Starters, Leavers and Movers
The basic processes surrounding the identity of employees are their entry into the company, their departure, and their change of department. They are often referred to as Starters, Leavers and Movers – SLAM for short. These core processes of identity management are about providing an identity with information and authorizations in a comprehensible, documented and controlled manner so that, for example, employees can start work immediately when they join the company (ideally on their first day). Here, it will be received as very positive by every new employee if there are no disruptive delays caused by missing authorizations or – even worse – missing hardware and a surprised IT department.
The latter in particular is often an indication that the processes initiated in HR do not harmonize properly with those from IT, or that there are even at least partially manual interfaces. Even the good old (one-dimensional) “entry checklist” has had its day in the age of digitization. Here, finely tuned processes that run simultaneously or interdependently (ideally automatically) are convincing and thus ensure that IT is not the last to know that a new colleague has started.
Authorization management in self-service
Even after joining the company and in the further course of employment, new authorizations are always necessary or should be removed or adapted. In this segment of identity management in particular, IT has in the past repeatedly assumed responsibility for adjustments to authorizations, as either no release mechanisms existed or, due to the system, release was only given by the IT manager. A rethink is very much in order, since especially in fast-moving times and with increased remote work, the IT manager – indeed, IT itself – no longer knows every employee personally.
How is it then possible to make a sensible decision in the release from IT as to whether an employee needs a certain authorization to perform his or her tasks? For this reason, we advise our customers in the processes to make the specialist departments responsible, since they can better assess the reasons for authorization requirements and also know the employees better. It is also easier to argue in the context of cost and performance accounting if the cost-bearing specialist department can decide for itself which software, hardware or which authorization should be set up.
The goal is to shift the decision to the responsible department and thus to where the decision can be made on the basis of figures, data and facts. This would create a self-service approach to self-management in the departments.
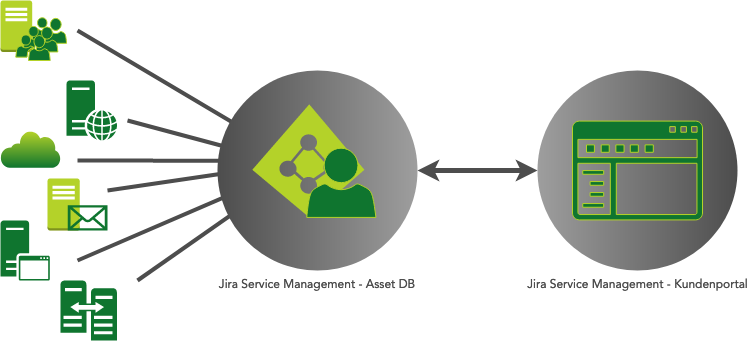
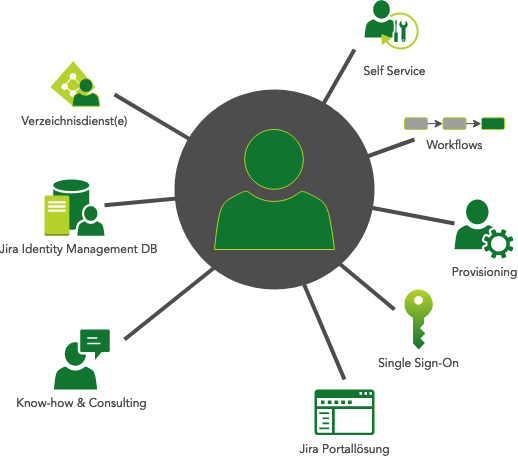
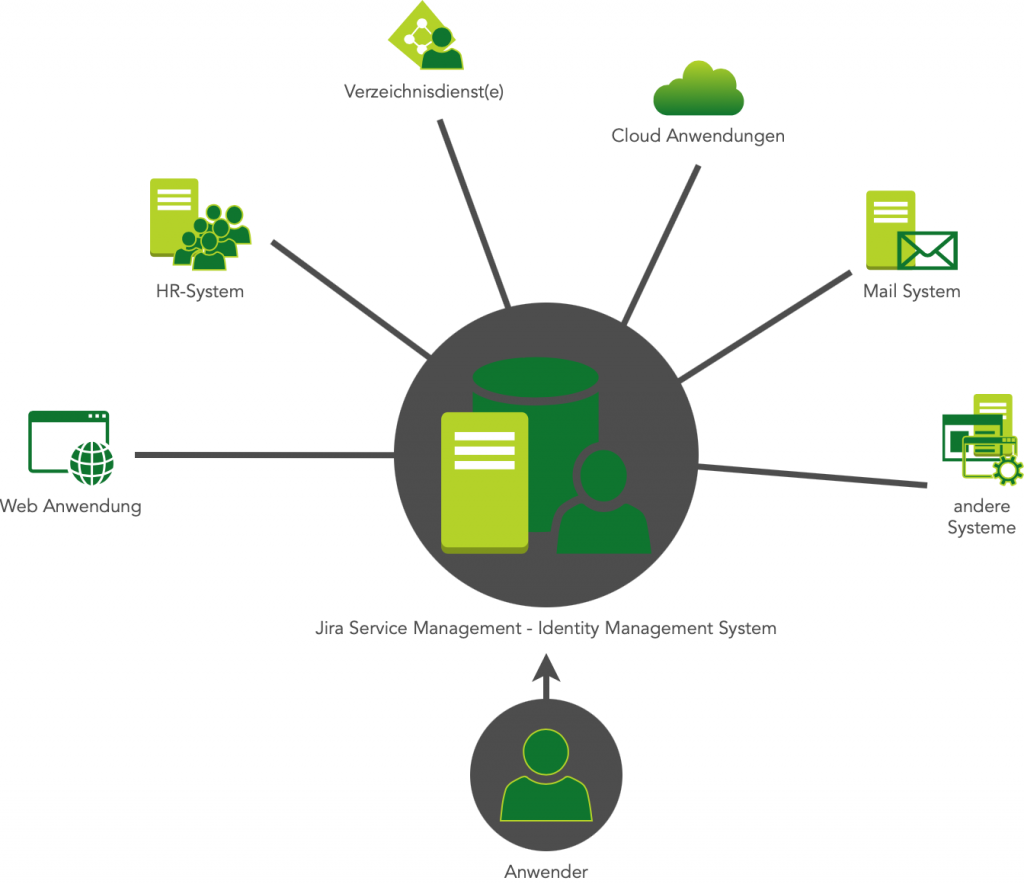
Jira Service Management – The Swiss Army Knife for Identity Management
The strength of Jira Service Management lies in its ability to connect smart and robust processes with information and data. The integration of Insight Asset Management, which was purchased by Atlassian last year, has set the course for even stronger integration between the powerful solution with customer portal and the Configuration Management Data Base (CMDB).
We have been implementing this solution approach for our customers for a long time and thus create not only very flexible processes – tailored to the customer’s requirements – but also easily extensible interfaces to systems and applications that benefit from identity management. Here we rely on standard interfaces such as Active Directory, LDAP, SSH, REST-API, PowerShell, SQL, etc. In projects, we like to proceed iteratively in cycles, so that the costs for the customer are plannable and manageable – with expectable performance and function blocks that can be used directly in operation.
In the next parts of this series of articles on identity management with Jira Service Management, you will learn how to use the capabilities of Jira Service Management to map powerful processes, automatically perform authorization requests directly in Active Directory or Red Hat Identity Management, and how the solution can be extended in the direction of asset inventory.